💻 Authentication
 Source: Hackndo
Source: Hackndo
📧 Key Message Exchanges
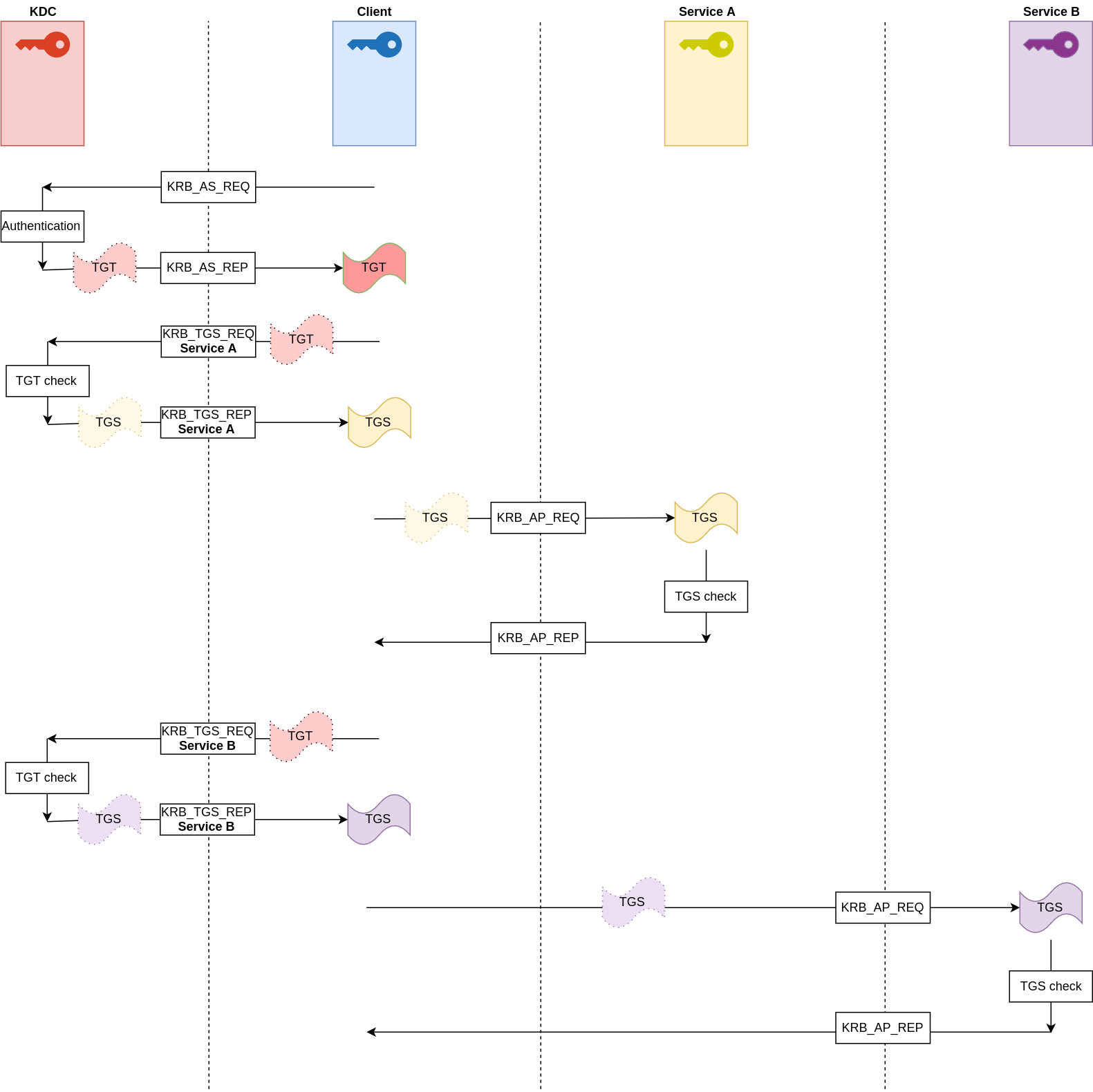
KRB_AS_REQ (Authentication Service Request)KRB_AS_REP (Authentication Service Reply)KRB_TGS_REQ (Ticket Granting Service Request)KRB_TGS_REP (Ticket Granting Service Reply)KRB_AP_REQ (Application Request)KRB_AP_REP (Application Reply)
🏁 Initial Authentication
KRB_AS_REQ (Authentication Service Request)
The client sends an AS-REQ message to the Authentication Service (AS) of the Key Distribution Center (KDC).
KRB_AS_REP (Authentication Service Reply)
The AS verifies the client's credentials and responds with an AS-REP message, which includes :
- The
TGT, encrypted with theKDC's secret key. - A
session keyfor the client, encrypted with theclient's password-derived key.
bash
kinit qu35t@RED.LAB🎫 Requesting a Service Ticket
KRB_TGS_REQ (Ticket Granting Service Request)
The client sends a TGS-REQ message to the Ticket Granting Service (TGS) of the KDC. This message includes :
- The
TGTobtained from the AS. - An
authenticator encryptedwith thesession keyfrom the AS-REP. - The
requested service principal name.
KRB_TGS_REP (Ticket Granting Service Reply)
The TGS verifies the TGT and the authenticator, then responds with a TGS-REP message, which includes :
- A
service ticket, encrypted with theservice's secret key. - A
session keyfor the client and the service, encrypted with the client's session key from the AS-REP.
bash
getST.py -spn MYSQLSvc/sqlsvc.red.lab:1433 -dc-ip 192.168.10.100 "RED.LAB"/"Administrator":"Password123"bash
Impacket for Exegol - v0.10.1.dev1+20240403.124027.3e5f85b - Copyright 2022 Fortra - forked by ThePorgs
[*] Getting ST for user
[*] Saving ticket in Administrator@MYSQLSvc_sqlsvc.red.lab:1433@RED.LAB.ccachebash
describeTicket Administrator@MYSQLSvc_sqlsvc.red.lab:1433@RED.LAB.ccachebash
Impacket for Exegol - v0.10.1.dev1+20240403.124027.3e5f85b - Copyright 2022 Fortra - forked by ThePorgs
[*] Number of credentials in cache: 1
[*] Parsing credential[0]:
[*] Ticket Session Key : e05489118ad4829d675cd1c5f8a0b969
[*] User Name : Administrator
[*] User Realm : RED.LAB
[*] Service Name : MYSQLSvc/sqlsvc.red.lab:1433
[*] Service Realm : RED.LAB
[*] Start Time : 18/07/2024 17:33:50 PM
[*] End Time : 19/07/2024 01:50:58 AM
[*] RenewTill : 19/07/2024 15:38:10 PM
[*] Flags : (0x40a10000) forwardable, renewable, pre_authent, enc_pa_rep
[*] KeyType : rc4_hmac
[*] Base64(key) : 4FSJEYrUgp1nXNHF+KC5aQ==
[*] Kerberoast hash : $krb5tgs$23$*USER$RED.LAB$MYSQLSvc/sqlsvc.red.lab~1433*$77582e1907fd08b0f65d60e9447c5470$477f8960c0d0936b339010daf6b1889166103329f8966f6eef8face65da1822268b40b851193afe3e6c06ba45e427c89731349a9fc949c8b28fb05d77de1d29f56c952ba74bd2d016af2e8cd8fb372dc6eb073f536603d549db20ef4d85baacdf0254b0c71c56afe4f5740c704258cb23738237768866a754d597973e5b242ee361b63bb21eaac49d24d7997489927faf513ef22f4310d20ad523d25ec10cbf07cad9b697470fb09f97ef144eeae95736899cbdeb4372386c3131f417e5ecfeaa9c8061c9c1179920885866fa2c719d98919417931889533b259bbc1cd9f83a640361fbb4fdbcb15f3eab08a6c70899d7fa43caafcc8291c96e18b5e6fef8fb69b36712780b12da81569a5858af6aca45de27ef0a47bb2e15d426f1daa2600691145039e8dda4ef7b6a809613659e0012380b7bb6ec91b47c21d502f4d06e5b84828e01fcae9957645ece4aa18f7ac50bf45339374ad71ce2b066678b9130f1a38b1d81cc3dbb56419f8699dc943fed9f6fb36bb118cf54fe168cc44bab5dc4c931640879c053f88845087f9334d32c2feb14dff306cdfd7f8120c494cbb545ff183e8a04e52d1fc070703bb2f6e3b605062db0f0952af18cdf665bf829830acce3c49f1f194f154a63c207e427b4a96fbf807a62f33d11c718fa8a8bff3d763eef18632376c02d707edcbfe342d138e491682d3b241656df8ac1c05a5c95258f58efe5c6700e52e2197305547ac30e7f42429775d2f6ae6d023aaa913f4286a35e718291288fc437b71c39785010fab4fa9832f5542b2611199395497c862978a7140f12ddc839a0710f908232485b14585a8adff2fb87786e4515ee0af7941b87036ec10a8c125c697ba39e3ddd5165fdb072dcac01279ed09c1a7a232411ca570f65f2ac137d63f62e7ec14e31d83a3f04cd6447d4e3a5a9dce73d14222fe1ad237e5861982469b81ed1942b59691e19b6284e3d38f434cf51a8656037a61970087ef7ce2573b33d9d6096c92bfdafb679baa184b15aed5741fa572ebe612d1c191321a7facf89ecd5a4789404aedd6ca143693ecae1cd601c2f5e7d1037dfff3373d3b528e0679dda6164c3f5a29fbb6b3eda9be8fa89ba36b03ec35b50fa94bf221cb7abc9997fab5a0f91c20593c1c17ab28498eccfad905f620d491ba06ad1d4568eece3aea1cd041e8db6ad8adee2fdc10ec6307f6b3c436f3f09c9a98d26a69bc162f2eb41445adcaa027d68101649d96ef632d72191b79632eeb66a457bb9f8aee7f4f29ec31c6d3316660d62297a8b7e72af18361259930ffb91be28a8b1282edd7f10ab7d5c3b424071997be4db4b527fab106a6fd851e9a4d733ed01a3e01e9be33f3e53afe6a24a1a98973dc90bbe86594b163c9854e619bf387b053eafa700d27d273ef739aebde24af4b722bd9be11084116dcee944f7f53091e7ba817648759bdba1b2e7e4e83ef5d0835fd08966460e887ba1222297cab95f0baae71bcc7d9f133869744e41731c1ed57508a3b9e700626853e2f274cc2da1f7cd5ed9822b089593735b1a535bb17389821931bcba8b8d3974b6df7d4e4e4753aa4e67455fb72bf98c846
[*] Decoding unencrypted data in credential[0]['ticket']:
[*] Service Name : MYSQLSvc/sqlsvc.red.lab:1433
[*] Service Realm : RED.LAB
[*] Encryption type : rc4_hmac (etype 23)
[-] Could not find the correct encryption key! Ticket is encrypted with rc4_hmac (etype 23), but no keys/creds were suppliedbash
export KRB5CCNAME=Administrator.ccachebash
klistbash
Ticket cache: FILE:Administrator.ccache
Default principal: Administrator@RED.LAB
Valid starting Expires Service principal
07/18/2024 17:48:00 07/19/2024 01:50:58 MYSQLSvc/sqlsvc.red.lab:1433@RED.LAB
renew until 07/19/2024 15:38:10🏆 Accessing the Service
KRB_AP_REQ (Application Request)
The client sends an AP-REQ message to the service. This message includes :
- The
service ticketobtained from the TGS. - An
authenticatorencrypted with the session key from the TGS-REP.
KRB_AP_REP (Application Reply)
The service verifies the service ticket and the authenticator, then responds with an AP-REP message, which includes :
- A
timestampencrypted with thesession key, confirming the client's identity.
